Shared
Hosting
We offer a Shared private network Microsoft Azure environment, but also support other hosting services such as AWS. Our solution takes care of your contingency plan for you. Backup data is stored as encrypted BLOB data via Azure storage accounts, where it can be synchronized to specific external locations if needed. Only authenticated persons have access. Data centers from Microsoft Azure with market standard compliance and with a regional presence.
Multi-Tenant
Manual Authentication via two-factor authentication
Data/Backup Encryption
Scalable hosting
Dedicated
Hosting
We offer a Dedicated private network Microsoft Azure environment, but also support other hosting services such as AWS. Our solution takes care of your contingency plan for you. Backup data is stored as encrypted BLOB data via Azure storage accounts, where it can be synchronized to specific external locations if needed. Only authenticated persons have access. Data centers from Microsoft Azure with market standard compliance and with a regional presence. Data centers from Microsoft Azure with market standard compliance and with a regional presence.
Single-Tenant
Manual Authentication via two-factor authentication or SSO/ADFS
Data/Backup Encryption
Scalable hosting
On-Premise
If you wish to host the solution on your own premise, we provide that option too. However, you must then proceed according to your own setup and Cenosco will not be responsible. With this option, you miss out on many benefits, as listed above. Concerned about security issues? Below you can explore our multi-layered security ring.
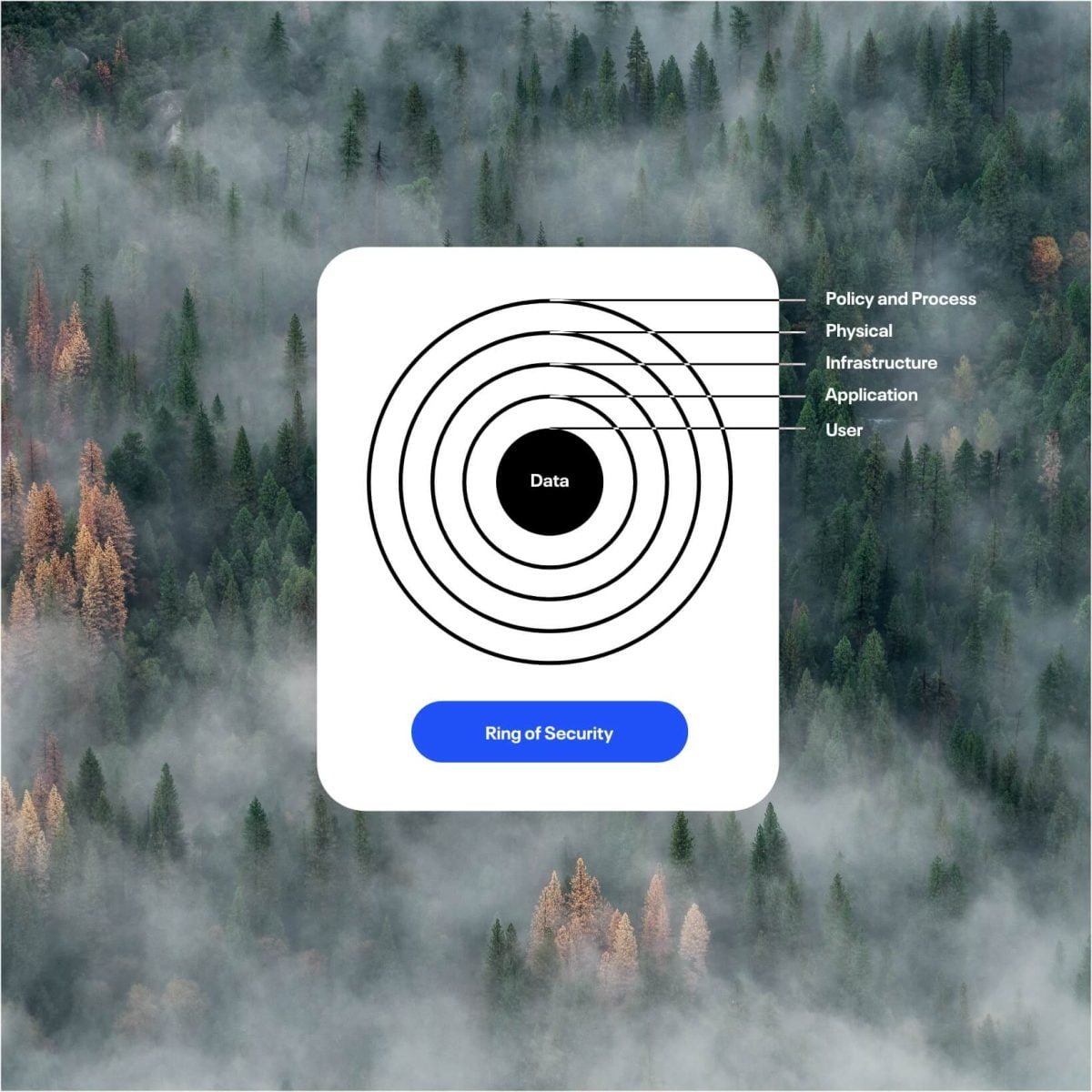
Security
As a Microsoft gold partner, we offer the latest and greatest in terms of security availability. We believe that a security system must be built from the ground up, and that’s why we have created the impenetrable Ring of Security. In order to protect and preserve the integrity of our customer data at all times, we focus on the physical, network and user levels of our service.

